How to Upload Files My Book Live Windows 10

Western Digital My Volume Live NAS owners worldwide found that their devices have been mysteriously mill reset and all of their files deleted.
WD My Volume Live is a network-fastened storage device that looks like a minor vertical volume that you can stand up on your desk. The WD My Book Live app allows owners to access their files and manage their devices remotely, even if the NAS is behind a firewall or router.
Today, WD My Volume Alive and WD My Book Live DUO owners worldwide suddenly found that all of their files were mysteriously deleted, and they could no longer log into the device via a browser or an app.
When they attempted to log in via the Web dashboard, the device stated that they had an "Invalid password."
"I have a WD My Book live connected to my home LAN and worked fine for years. I have just found that somehow all the data on information technology is gone today, while the directories seems in that location simply empty. Previously the 2T volume was virtually full but at present it shows full capacity," a WD My Volume owner reported on the Western Digital Customs Forums.
"The even foreign thing is when I endeavour to log into the control UI for diagnosis I was-only able to get to this landing page with an input box for "owner countersign". I take tried the default password "admin" and also what I could ready for information technology with no luck."
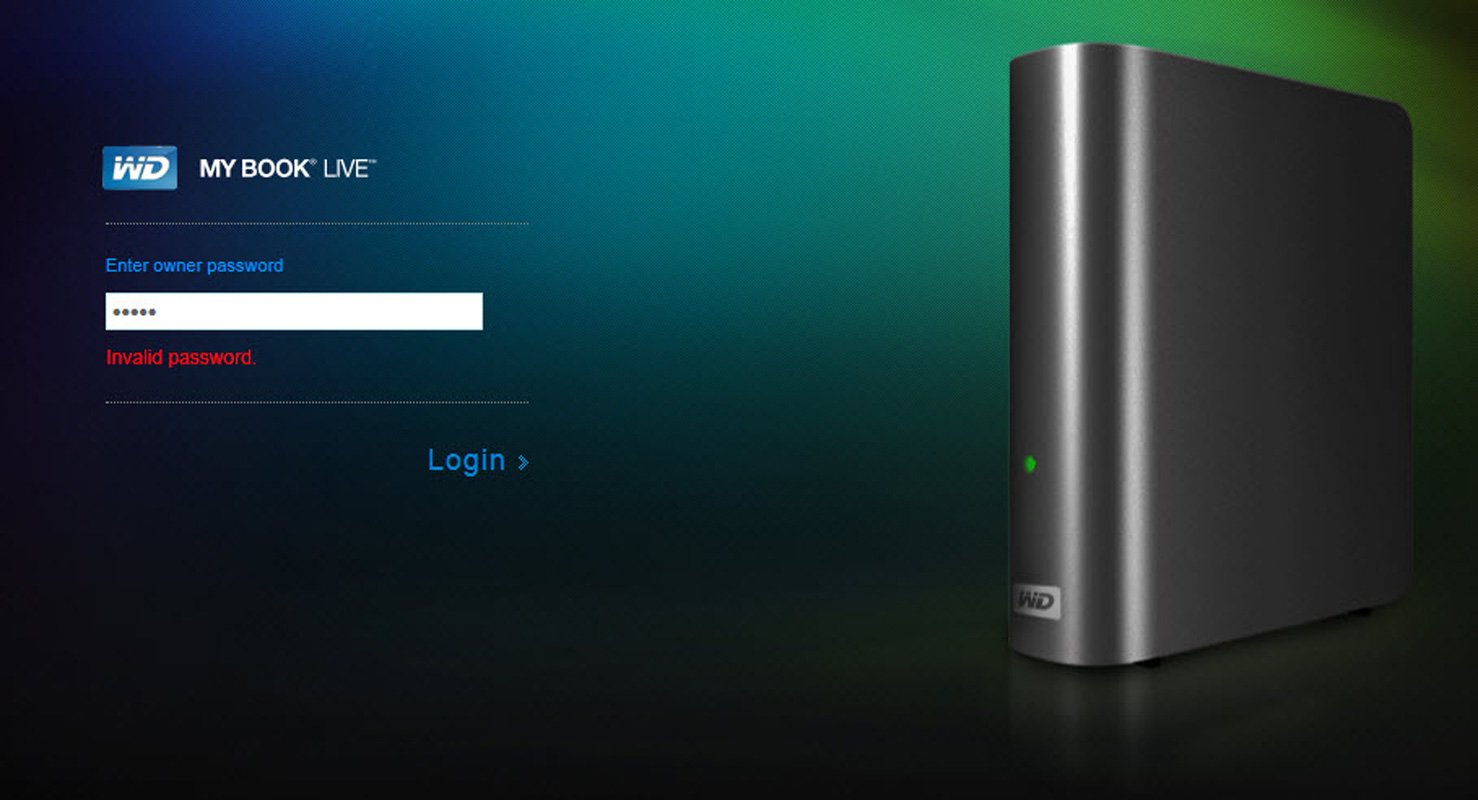
Source: WD Forum
My Book Live devices issued a manufactory reset command
After further owners confirmed that their devices suffered the same upshot, owners reported that the MyBook logs showed that the devices received a remote command to perform a factory reset starting at effectually iii PM yesterday and through the nighttime.
"I have found this in user.log of this drive today:
Jun 23 15:xiv:05 My BookLive factoryRestore.sh: begin script:
Jun 23 15:fourteen:05 My BookLive shutdown[24582]: shutting down for arrangement reboot
Jun 23 16:02:26 My BookLive S15mountDataVolume.sh: brainstorm script: start
Jun 23 16:02:29 My BookLive _: pkg: wd-nas
Jun 23 16:02:30 My BookLive _: pkg: networking-general
Jun 23 16:02:30 My BookLive _: pkg: apache-php-webdav
Jun 23 xvi:02:31 My BookLive _: pkg: date-fourth dimension
Jun 23 sixteen:02:31 My BookLive _: pkg: alerts
Jun 23 16:02:31 My BookLive logger: hostname=My BookLive
Jun 23 sixteen:02:32 My BookLive _: pkg: admin-residual-api
I believe this is the culprit of why this happens…No one was fifty-fifty dwelling house to use this drive at this fourth dimension…"
Unlike QNAP devices, which are unremarkably connected to the Cyberspace and exposed to attacks such as the QLocker Ransomware, the Western Digital My Book devices are stored behind a firewall and communicate through the My Book Live cloud servers to provide remote access.
Some users have expressed concerns that Western Digital's servers were hacked to allow a threat actor to push out a remote manufactory reset control to all devices continued to the service.
If a threat histrion wiped devices, it is strange as no one has reported ransom notes or other threats, pregnant the attack was simply meant to be destructive.
Some users afflicted by this attack have reported success recovering some of their files using the PhotoRec file recovery tool.
Unfortunately, other users accept non had equally much success.
If yous own a WD My Book Live NAS device, Western Digital strongly recommends that you disconnect the device from the Net.
"At this fourth dimension, we recommend y'all disconnect your My Book Alive and My Book Live Duo from the Internet to protect your data on the device," Western Digital said in an informational.
Unpatched vulnerability believed to exist behind attacks
In a statement shared with BleepingComputer, Western Digital has determined that My Book Alive and My Book Live Duo devices connected straight to the Internet are are being targeted using a remote code execution vulnerability.
Western Digital has determined that some My Book Live and My Book Live Duo devices are being compromised through exploitation of a remote control execution vulnerability. In some cases, the attackers have triggered a factory reset that appears to erase all data on the device.
We are reviewing log files which we accept received from afflicted customers to further characterize the assault and the mechanism of admission. The log files we have reviewed show that the attackers direct continued to the affected My Book Alive devices from a variety of IP addresses in different countries. This indicates that the affected devices were direct accessible from the Cyberspace, either through direct connection or through port forwarding that was enabled either manually or automatically via UPnP.
Additionally, the log files show that on some devices, the attackers installed a trojan with a file named ".nttpd,1-ppc-exist-t1-z", which is a Linux ELF binary compiled for the PowerPC compages used by the My Volume Alive and Live Duo. A sample of this trojan has been captured for further analysis and it has been uploaded to VirusTotal.
Our investigation of this incident has non uncovered whatever evidence that Western Digital cloud services, firmware update servers, or customer credentials were compromised. As the My Book Alive devices can be directly exposed to the internet through port forwarding, the attackers may exist able to discover vulnerable devices through port scanning.
Nosotros empathize that our customers' data is very important. We exercise not yet sympathize why the attacker triggered the manufacturing plant reset; however, we take obtained a sample of an affected device and are investigating farther. Additionally, some customers have reported that data recovery tools may exist able to recover data from afflicted devices, and we are currently investigating the effectiveness of these tools.
The WD My Book Live devices received their final firmware update in 2015.
Since and so, a remote code execution vulnerability tracked every bit CVE-2018-18472 was disclosed along with a public proof-of-concept exploit.
It is believed that a threat actor performed a mass browse of the Net for vulnerable devices and used this vulnerability to issue the mill-reset control.
Update six/24/21: Added statement from Wester Digital
Update 6/25/21: Added data about vulnerability and recovery options.
Update half dozen/26/21: Added full updated statement.
Thx to Tim from desert datarecovery for the tip.
Source: https://www.bleepingcomputer.com/news/security/wd-my-book-nas-devices-are-being-remotely-wiped-clean-worldwide/
0 Response to "How to Upload Files My Book Live Windows 10"
Postar um comentário